For the last decade, it's been impossible to talk about the world of development and operations without mentioning 'Docker.' It popularized the concept of containers and completely transformed the way we deploy and run applications. But no king reigns forever. In recent years, a tool has emerged that confidently answers the question, "Can we use containers without Docker?" with a resounding "Yes!" That tool is **Podman**, developed under the leadership of Red Hat. 🐳
Some of you might be sighing, "Do I have to learn another new thing?" But Podman isn't just 'another container tool.' It's an ambitious project that inherits the strengths of the container ecosystem built by Docker while aiming to solve the structural limitations that have been pointed out. A lighter, more secure container engine that moves like a part of the Linux system itself. This is the core identity of Podman. In this article, we'll dive deep to see if Podman can truly be the game-changer that ends the Docker era.
1. What is Podman? No 'Daemon,' You Say?
The most crucial keyword to understanding Podman is **'Daemonless.'** If you've used Docker, you know that a background process, `dockerd`, is always running on your system. We, as users, use the `docker` client command to ask this daemon to "spin up a container," and the daemon handles all the dirty work.
This approach is convenient but has some inherent problems. First, it's a **Single Point of Failure**. If `dockerd` stops or malfunctions for any reason, all containers running on that server are affected. 😱 Second, there's a **security concern**. The daemon runs with `root` privileges by default. This means if a vulnerability is found in the daemon itself or if its API is improperly exposed, the entire system could be at risk. A worst-case scenario involves an attacker escaping from a container to gain `root` access on the host.
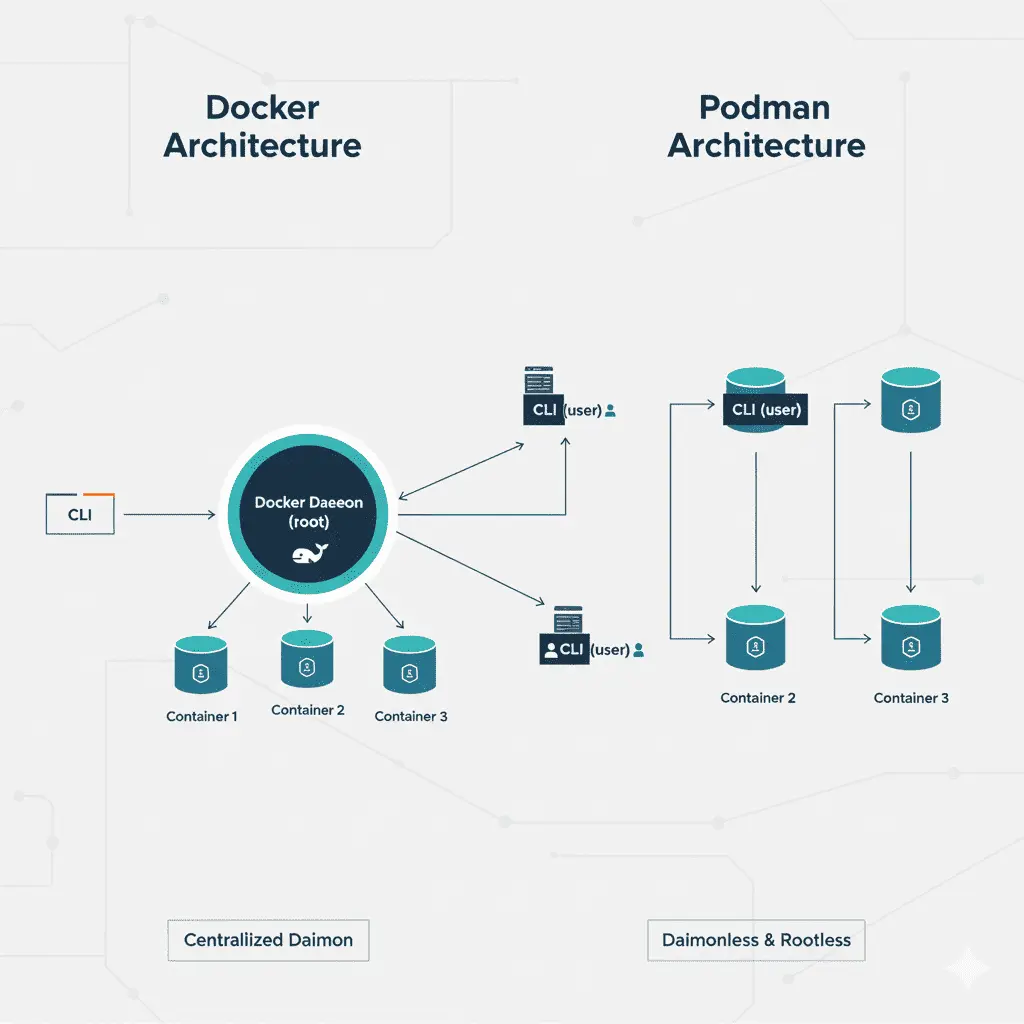
Podman tackles this problem head-on. It eliminates the central management daemon. When a user enters a command, Podman launches the container directly as a child process, just like any other Linux process. This brings several huge advantages:
- Enhanced Security: No daemon means no daemon-related vulnerabilities. Furthermore, Podman is designed to run in **rootless mode** by default, meaning containers run with standard user privileges. If a container is compromised, the attacker only gains the permissions of that user, not control of the entire system.
- System Integration: Without a daemon as a middleman, containers are treated like regular processes on the system. This leads to fantastic integration with `systemd`, Linux's standard service manager. It becomes much easier to register and manage containers as regular services.
- Transparency: You can directly see and manage running container processes using standard Linux commands like `ps` and `top`. Containers are no longer 'magic boxes' but predictable, ordinary processes.
2. The Main Event: Podman vs. Docker, What's Different?
One of Podman's biggest strengths is its consideration for Docker users. Most Docker commands work identically in Podman. You can even set an alias like `alias docker=podman` and use your existing scripts with minimal changes. But don't be fooled by the similar exterior; the internals are quite different. Here’s a table summarizing the key differences.
| Feature | Podman | Docker |
|---|---|---|
| Architecture | Daemonless The user directly runs container processes. Each container is an independent child process. |
Client-Server (Daemon) A central `dockerd` daemon running in the background manages everything. |
| Security (Default) | ✔ Rootless-first Runs containers with normal user privileges. High level of isolation from the host system. |
✖ Requires Root Privileges The daemon runs as root, and the user must be in the `docker` group. Potential security risk. |
| System Integration | ✔ Excellent (`systemd`) Easily generate `systemd` unit files from containers or Pods to manage them as services. |
✖ Limited The daemon itself can be managed by `systemd`, but integrating individual containers is cumbersome. |
| Multi-Container Management | Pods Natively supports the Kubernetes 'Pod' concept. Groups multiple containers to be managed as a single unit. |
Docker Compose Defines and runs multi-container applications through a separate `docker-compose.yml` file. |
| Orchestration | Kubernetes-Oriented Pod definitions can be easily exported to Kubernetes YAML files, aligning local dev with production. |
Docker Swarm Includes its own orchestration tool, Swarm. (Usage has declined as Kubernetes became the standard). |
| Ecosystem & Community | Growing Rapidly growing with strong backing from Red Hat. Dominant in enterprise Linux environments. |
Mature and Vast A massive user base, extensive documentation, tutorials, and third-party tools form a well-established ecosystem. |
Key Takeaway: Docker is like a 'VM', Podman is like a 'Process'
As a simple analogy, Docker feels like an independent 'virtual machine manager' for containers. Everything goes through the central daemon. In contrast, Podman treats containers like 'regular processes' that are part of the system. This philosophical difference is the source of all other distinctions in security, integration, and more.
3. Getting Hands-On: Installing and Using Podman
Seeing is believing. Let's install and use Podman. Fortunately, it can be installed with a simple command on most Linux distributions.
Linux (Fedora/RHEL/CentOS)
sudo dnf install podmanLinux (Debian/Ubuntu)
sudo apt-get update
sudo apt-get -y install podmanmacOS & Windows
On macOS and Windows, Podman runs on a Linux virtual machine. The easiest way is to install Podman Desktop, or install the CLI via Homebrew (macOS) or WSL2 (Windows).
# macOS with Homebrew
brew install podman
# Initialize and start the Podman machine
podman machine init
podman machine startOnce installed, try running your usual Docker commands, just replacing `docker` with `podman`. You'll be surprised at how seamlessly it works.
# Search for an image (on Docker Hub)
podman search nginx
# Pull an image
podman pull docker.io/library/nginx
# List downloaded images
podman images
# Run an Nginx container (forwarding to port 8080)
podman run --name my-nginx -p 8080:80 -d nginx
# List running containers
podman ps
# Check container logs
podman logs my-nginx
# Stop and remove the container
podman stop my-nginx
podman rm my-nginxEasy, right? If your muscle memory is stuck on `docker`, just add `alias docker=podman` to your shell's config file (`.bashrc`, `.zshrc`, etc.). Just like that, you're a Podman user without even realizing it! 😉
4. Voices from the Trenches: The Reddit Community Reacts
When adopting new technology, the first thing we want to know is, "What do actual users think?" So, I browsed through developer hangouts like Reddit's `/r/selfhosted` and `/r/devops`. The discussions around Podman were quite heated.
"I use it because: no additional fees for customers running it in business instances with > 250 employees; no additional tech support costs (included with existing Red Hat Subs); daemonless; easier to build config that ports to K8s easily; not happy with Docker's support and customer service the few times I have used them."
– Reddit UserOf course, it's not all praise. In the early days, there were complaints about the stability of `podman-compose` and an ecosystem that wasn't as mature as Docker's. Some users also voiced difficulties with performance or network configuration, especially on macOS and Windows.
"Had issues with dependent containers last I tried and spent a lot of time troubleshooting. But decided what's the point it already works reliably in docker. And yes I was using quadlets."
– Reddit User u/Legitimate_Square941Overall, the community sentiment can be summarized as: **'If you prioritize security and deep integration with systemd in a Linux server environment, Podman is the best choice. However, Docker's vast ecosystem, maturity, and simplicity, especially for desktop environments, cannot be ignored.'** It's also important to note that many of the early issues are being resolved as the technology matures.
5. Podman's Secret Weapons: Pods and systemd Integration
If you think of Podman as just a 'daemonless version of Docker,' you're missing its true potential. Podman has two powerful weapons in its arsenal.
Weapon 1: Native Pod Support
If you've used Kubernetes, you're familiar with the concept of a 'Pod.' A Pod is a group of one or more containers that share resources like networking and storage. For example, you can bundle a web application container with a sidecar container that collects its logs into a single Pod to be deployed and managed together.
In Docker, you can configure a similar environment with `docker-compose`, but that's a Docker-specific method. Podman, however, can natively create and run Kubernetes-style Pods in your local environment!
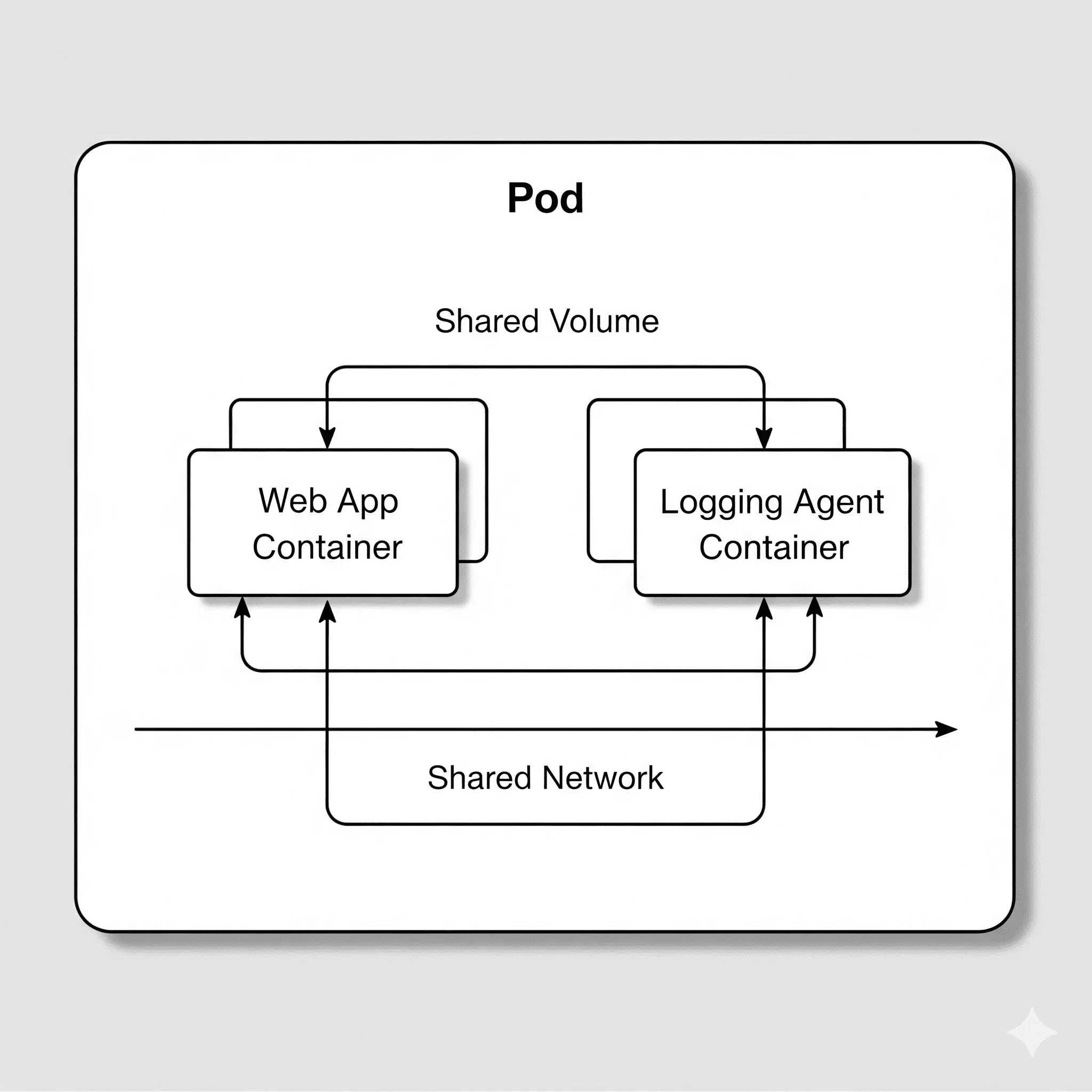
# Create a new pod named 'my-app-pod' and publish port 8080
podman pod create --name my-app-pod -p 8080:80
# Add a wordpress container to the 'my-app-pod'
podman run -d --pod my-app-pod --name my-wordpress wordpress
# Add a MySQL container to the 'my-app-pod'
podman run -d --pod my-app-pod --name my-db -e MYSQL_ROOT_PASSWORD=secret mysql
# Check running pods
podman pod ps
The true power of this comes from the `podman generate kube` command. It automatically generates a Kubernetes-compatible YAML file based on the Pod you just created. This dramatically reduces the gap between your local development environment and the actual production environment. 🚀
Weapon 2: Perfect systemd Integration
Anyone who has managed a server knows how powerful `systemd` is. It's the heart of Linux, handling service auto-starts, restarts, dependency management, and more. Podman has built-in functionality to turn a container or a Pod into a `systemd` service.
# Generate a systemd unit file for the 'my-nginx' container
podman generate systemd --name my-nginx --files
# Copy the generated .service file to the system directory
sudo cp container-my-nginx.service /etc/systemd/system/
# Reload the systemd daemon and enable/start the service
sudo systemctl daemon-reload
sudo systemctl enable --now container-my-nginx.service
# Check the service status
systemctl status container-my-nginx.service
Now, the `my-nginx` container is a full-fledged system service that will start automatically on boot and restart if it fails. No more complex scripts or third-party tools are needed. This is what it means when we say Podman 'integrates with the system.'
Conclusion: Should You Ditch Docker for Podman?
It's been a long journey. Now it's time to answer the final question. Can Podman really bring an end to the Docker era?
My answer is, 'It depends, but the chances are very high.'
I strongly recommend switching to Podman if you fall into these categories:
- Security is your top priority: In environments like finance or government, rootless containers are becoming a necessity, not a choice.
- You heavily utilize Linux servers and systemd: If you want to perfectly integrate containers as part of your system services, there's no better alternative than Podman.
- Your end goal is Kubernetes: Using the Pod concept from the local development stage will minimize the differences with your production environment, making Podman the perfect partner.
- You primarily use Red Hat-family Linux (RHEL, CentOS, Fedora): It's already included as the default container engine and offers the best compatibility.
However, Docker might still be a good choice in these cases:
- A mature and vast ecosystem is important: The wealth of tutorials, blog posts, and third-party tools that Docker has accumulated over the years is undeniable. Docker can still be more beginner-friendly.
- You rely on Docker Swarm as your core orchestration tool: Podman does not support Swarm.
- Your entire team is deeply familiar with a Docker workflow: You must consider the learning curve and the cost of changing existing pipelines.
- Your main purpose is simple container execution on a desktop (macOS, Windows): While Podman supports desktops, the user experience and convenience of Docker Desktop are still very strong.
"Podman is less of a 'replacement' for Docker and more of an 'evolution.' It respects the ecosystem by sharing the OCI standard for containers but presents a better architecture and security model."
In conclusion, Podman not only threatens Docker's throne but also shows the direction in which container technology is heading. Even if you don't switch everything today, why not start by tasting its appeal with a simple `alias docker=podman`? You might just find yourself falling in love with the freedom of a daemonless world.

"I think, podman is far superior when it comes to containerized applications. The rootless implementation is much better, and it integrates better into the existing system/infrastructure. docker behaves more like a hypervisor that you have to tell what to do. podman is running pretty much transparently and you wouldn't really know if it's running in a container or not. Understanding podman also gives you a better understanding what containers are... God I love quadlets..."
– Reddit User u/luuuuuku